Donuts signs up to Architelos anti-abuse service
Architelos has a secured its first major customer win for the NameSentry anti-abuse service that it launched back in August.
Donuts, the highest-volume portfolio gTLD applicant, has signed up for the service, according to the companies.
For Donuts, which is probably the applicant that makes opponents of new gTLDs the most nervous, it’s another chance to show that it’s serious about operating clean zones.
For Architelos, it’s a pretty significant endorsement of its new technology.
The NameSentry service aggregates abuse data from multiple third-party malware, spam and phising lists and presents it in a way that makes it easier for registries shut down bad behavior.
Architelos launches new gTLD anti-abuse tool
Architelos, having consulted on about 50 new gTLD applications, has refocused on its longer-term software-based game plan with the recent launch of a new anti-abuse tool for registries.
NameSentry is a software-as-a-service offering, currently being trialed by an undisclosed number of potential customers, designed to make it easier to track abusive domains.
Architelos gave us a demo of the web site yesterday.
The service integrates real-time data feeds from up to nine third-party blocklists – such as SURBL and SpamHaus – into one interface, enabling users to see how many domains in their TLD are flagged as abusive.
Users can then drill down to see why each domain has been flagged – whether it’s spamming, phishing, hosting malware, etc – and, with built-in Whois, which registrar is responsible for it.
There’s also the ability to generate custom abuse reports on the fly and to automate the sending of takedown notices to registrars.
CEO Alexa Raad and CTO Michael Young said the service can help streamline the abuse management workflow at TLD registries.
Currently, Architelos is targeting mainly ccTLDs – there’s more of them – but before too long it expects start signing new gTLD registries as they start coming online.
With many new gTLD applicants promising cleaner-than-clean zones, and with governments leaning on their ccTLDs in some countries, there could be some demand for services such as this.
NameSentry is priced on a subscription basis, based on the size of the TLD zone.
Is .city confusingly similar to .citi? UDRP says yes
In one of the more surprising twists to hit the new gTLD program, Citigroup has claimed that its proposed dot-brand gTLD, .citi, is not “confusingly similar” to the proposed generic gTLD .city.
The company appears to be trying to avoid getting into a contention set with the three commercial applicants for .city, which would likely put it into an expensive four-way auction.
It’s a surprising move because you’d expect a financial services company to want to at least try to mitigate the risk of future .city/.citi typo-based phishing attacks as much as possible.
Indeed, its .citi application states that the mission of the gTLD “is to further assist Applicant in accomplishing its mission of providing secure online banking and financial services”.
Nevertheless, the company is now arguing, in a few comments filed with ICANN today, this:
CITI and CITY are not so similar in an Internet context as to create a probability of user confusion if they are both delegated into the root zone. Thus, the .CITI application should not be placed into a contention set with the .CITY application.
The new Citigroup position is especially bewildering given that it has argued the exact opposite — and won — in at least two UDRP cases.
In the 2009 UDRP decision Citigroup Inc. v. Domain Deluxe c/o Domain Administrator, Citigroup contended that:
Respondent’s citywarrants.com domain name is confusingly similar to Complainant’s CITIWARRANTS mark.
The panelist in the case concluded that the Y variant of the name was merely a “mistyped variation” of and “substantively identical” to the Citigroup trademark.
A similar finding appears to have been handed down in Citigroup v Yongki, over the arguably generic citycard.com, but the decision is written in Korean so I can’t be certain.
The company’s current view, which I’m going to go out on a limb on and characterize as expedient, is that ICANN has delegated multiple ccTLDs that have only one character of variation in the past (it hasn’t — the ccTLDs it cites all pre-date ICANN) without causing confusion.
It also states in its comments that the meaning and proposed usage of the two strings is “very different” (which one commenter has already suggested is historically dubious).
So what’s going on here?
Is Citigroup really willing to risk potential phishing problems down the line to save a few measly bucks today? On the face of it, it looks that way.
If it is put in a contention set with the three .city applicants, it could wind up at auction against Donuts ($100m funding), TLD Registry Ltd (apparently backed by the Vision+ fund) and Directi.
Will Citigroup’s gambit pay off?
That’s down to a) the String Similarity Panel and b) whether any of the .city applicants tries to force the company into the contention set via a String Confusion Objection, which seems unlikely.
The first .xxx phishing site?
Those readers following @domainincite on Twitter may have noticed I spent a lot of time on Friday Googling for .xxx web sites, to get an idea how the new namespace is being used.
All in the name of research, of course.
As well as the expected video, dating and forum sites, I found one or two inexplicably safe-for-work oddities.
I also found what I believe may be the first .xxx site set up for phishing.
The domain name signin.xxx, registered to an individual in Ohio, looks extremely suspicious, especially when you consider the subdomains the registrant has created.
Here’s a screenshot of the URL www.hotmail.com.signin.xxx:
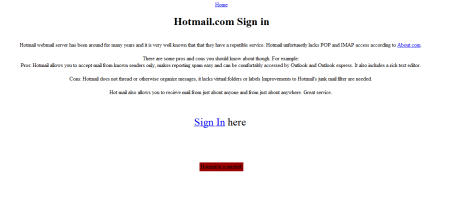
I have no evidence that the site has been used in a phishing attack, or that the registrant intends to use it in one. However, it seems pretty clear that he’s noticed the potential for abuse.
The page’s footer offers to sell the domain for a seven-figure sum.
Will new gTLDs really increase phishing?
The US Federal Trade Commission has come out swinging against ICANN’s new generic top-level domains program, saying it will increase online fraud and should be scaled back.
In an open letter to ICANN’s top brass yesterday, the FTC’s four commissioners claimed that “the dramatic introduction of new gTLDs poses significant risks to consumers”.
Saying that more gTLDs will make it easier for scammers to acquire domain names confusingly similar to existing brands, the commissioners said the program should be rolled out as a limited pilot.
The FTC commissioners wrote (pdf):
A rapid, exponential expansion of gTLDs has the potential to magnify both the abuse of the domain name system and the corresponding challenges we encounter in tracking down Internet fraudsters. In particular, the proliferation of existing scams, such as phishing, is likely to become a serious challenge given the infinite opportunities that scam artists will now have at their fingertips. Fraudsters will be able to register misspellings of businesses, including financial institutions, in each of the new gTLDs, create copycat websites, and obtain sensitive consumer data with relative ease before shutting down the site and launching a new one.
The letter demands better Whois accuracy enforcement, better ICANN compliance programs, and a cap on approved new gTLDs in the first round perhaps as low as a couple dozen.
The FTC’s claims that new gTLDs will increase phishing may not be supported by reality, however.
The latest data (pdf) from the Anti-Phishing Working Group shows that in the first half of the year only 18% of domain names used in phishing attacks were registered by the attacker.
That was down from 28% in the second half of 2010. Phishers are much more likely to compromise a domain belonging to somebody else – by hacking a web server, for example.
Of the 14,650 maliciously registered domains 10,444 (70%) were used to phish Chinese targets, “overwhelmingly” the e-commerce site Taobao.com, the APWG found.
Furthermore, only 2% of these domains – just 1,816 over six months – were judged to have been registered due to their confusing similarity with the brands they target.
The APWG said (emphasis in the original):
These are the lowest numbers we have observed in the last past four years, and show that using domain names containing brand strings has fallen further out of favor among phishers.
…
the domain name itself usually does not matter to phishers, and a domain name of any meaning, or no meaning at all, in any TLD, will usually do. Instead, phishers almost always place brand names in subdomains or subdirectories
The APWG found only one gTLD that ICANN has introduced – .info, with 4.5% – in its top ten phishing TLDs. The .com space accounts for 48.9% of all phishing domains.
Will the increase in the number of gTLDs reverse these trends? The FTC seems to think so, but the claims in its letter appear to be based largely on guesswork and fear rather than data.
I suspect that the FTC’s letter is more concerned with ICANN’s ongoing bilateral talks with registrars over law enforcement-demanded amendments to the Registrar Accreditation Agreement.
These talks are completely separate and distinct from the new gTLDs program policies, but in the last few weeks we’ve seen them being repeatedly conflated by US lawmakers, and now the FTC.
This may be ignorance, but it could just as well be an attempt to apply political pressure on ICANN to make sure the RAA talks produce the results law enforcement agencies want to see.
ICANN does not want to be forced into an embarrassing retreat on its hard-fought gTLD expansion. By producing a strong RAA, it could deflect some of the concerns about the program.
BITS may apply for six financial gTLDs
BITS, the technology policy wing of the Financial Services Roundtable, may apply to ICANN for as many as six financially-focused new top-level domains.
The organization is pondering bids for .bank, .banking, .insure, .insurance, .invest and .investment, according to Craig Schwartz, who’s heading the project as general manager for registry programs.
(UPDATE: To clarify, these are the six strings BITS is considering. It does not expect to apply for all six. Three is a more likely number.)
Schwartz, until recently ICANN’s chief gTLD registry liaison, told DI that the application(s) will be filed by a yet-to-be-formed LLC, which will have the FSR and the American Bankers Association as its founding members.
It will be a community-designated bid, which means the company may be able to avoid an ICANN auction in the event that its chosen gTLD strings are contested by other applicants.
“We’ve looked at the scoring, and while it may not come into play at all we do believe we can meet the requisite score [for a successful Community Priority Evaluation],” Schwartz said. “But we’re certainly mindful of what’s happening in the space, there’s always the possibility of contention.”
There’s no relationship between BITS and CORE, the Council of European Registrars, which is apparently looking into applying for its own set of financially-oriented gTLDs, Schwartz said.
It’s not a big-money commercial play, but the new venture would be structured as a for-profit entity, he said.
“It’s relatively analogous to what’s happened in the .coop space, where after 10 years they have only about 7,000 registrations,” Schwartz said.
It sounds like pricing might be in the $100+ range. Smaller financial institutions lacking the resources to apply for their own .brand gTLDs would be a likely target customer base.
Interestingly, .bank may begin life as a business-to-business play, used primarily for secure inter-bank transactions, before it becomes a consumer-facing proposition, Schwartz said.
He added that it would likely partner with a small number of ICANN-accredited registrars – those that are able to meet its security requirements – to get the domains into the hands of banks.
VeriSign has already signed up to provide the secure back-end registry services for the bid.
UDRP reform effort begins
ICANN has kicked off a review of its Uniform Dispute Resolution Policy, the occasionally controversial process used to adjudicate cybersquatting complaints.
The GNSO Council on Thursday voted to ask ICANN staff for a so-called “Issues Report” on UDRP, indicating that reform of the process is likely.
This is the relevant portion of the resolution, passed unanimously:
RESOLVED #2, the GNSO Council requests an Issues Report on the current state of the UDRP. This effort should consider:
* How the UDRP has addressed the problem of cybersquatting to date, and any insufficiencies/inequalities associated with the process.
* Whether the definition of cybersquatting inherent within the existing UDRP language needs to be reviewed or updated. The Issue Report should include suggestions for how a possible PDP on this issue might be managed.
Issues Reports commissioned by the Council are expected within 15 days, and 15 days after that the Council is expected to vote on whether to kick off a Policy Development Process.
A PDP could lead to changes to the UDRP that would be binding on all ICANN-accredited registrars and their customers.
While the UDRP has proven very effective at dealing with clear-cut cases of cybersquatting over the last 12 years, critics claim that it is often interpreted too broadly in favor of trademark interests.
If you read this blog regularly, you’ll know I frequently report on unfathomable UDRP decisions, but these are generally the exception rather than the rule.
Unrelated to UDRP, the GNSO Council has also voted against asking ICANN for an Issues Report on registry/registrar best practices for mitigating domain abuse.
Business interests wanted registrars to take more measures (voluntarily) to curb activities such as phishing, but registrars think this kind of rule-making is beyond the scope of the GNSO.
After a lot of heated debate and arcane procedural wrangling, the Council decided instead to ask for a “discussion paper”, a term that has no meaning under ICANN’s rules, meaning a PDP is less likely.
Russian domain crackdown halves phishing attacks
Phishing attacks from .ru domains dropped by almost half in the second quarter, after tighter registration rules were brought in, according to new research.
Attacks from the Russian ccTLD namespace fell to 528, compared to 1,020 during the first quarter, according to Internet Identity’s latest report.
IID attributed the decline to the newly instituted requirement for all registrants to provide identifying documents or have their domains cancelled, which came into effect on April 1.
The report goes on to say:
Following a similar move by the China Internet Network Information Center in December 2009, spam researchers suggested that this tactic only moves the criminals to a new neighborhood on the Internet, but has no real impact on solving the problem.
I wonder whose ccTLD is going to be next.
The IID report also highlights a DNS redirection attack that took place in June in Israel, which I completely missed at the time.
Apparently, major brands including Microsoft and Coca-Cola started displaying pro-Palestine material on their .co.il web sites, for about nine hours, after hackers broke into their registrar accounts at Communigal.







Recent Comments